Using the Live Data Search tool
The Live Data Search tool in Dark Web ID is a prospecting feature designed for managed service providers (MSPs) to generate sales leads by highlighting dark web-related risks to potential clients. Users can enter a client's domain, and the tool will display data that has been recently compromised, including masked passwords, usernames, and personally identifiable information (PII). This tool produces exportable reports that feature branded infographics, helping MSPs effectively communicate these risks to clients and address security gaps.
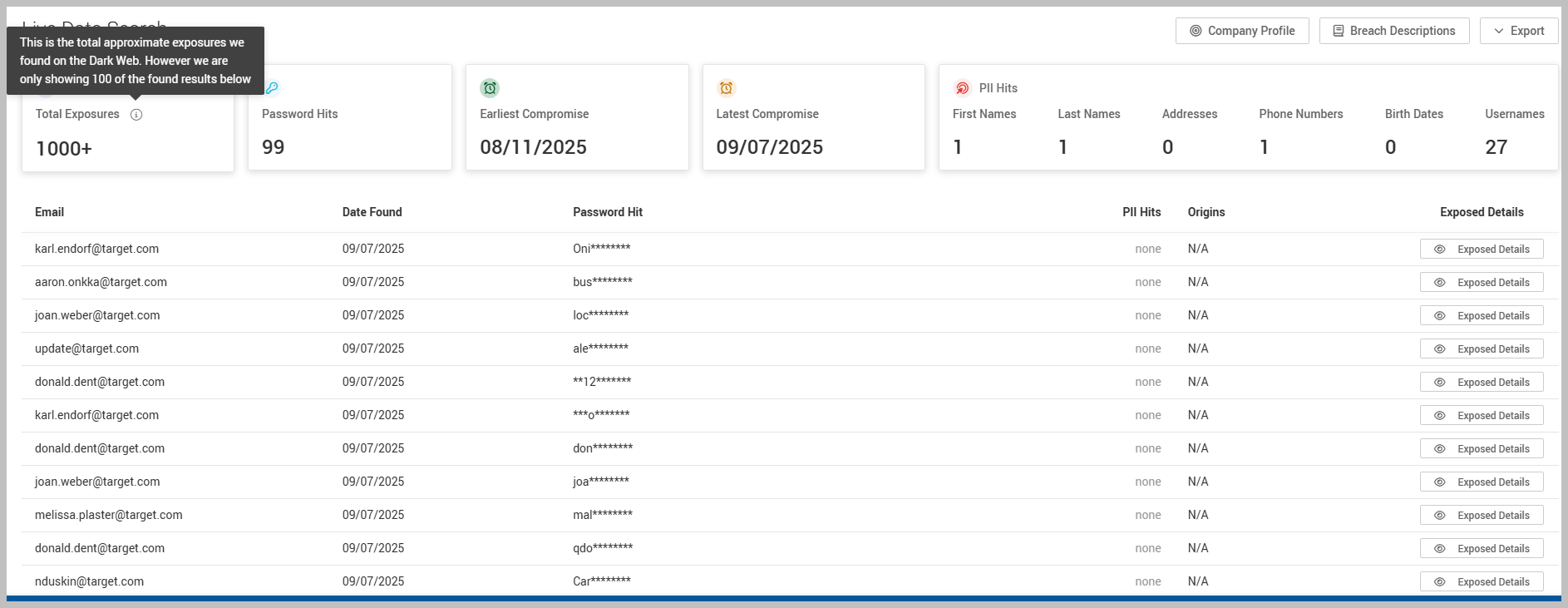
The Live Search tool generates a sample dataset comprising the 100 most recent records from the past 24 months. In compliance with current privacy laws, the tool will display only the first four characters of any exposed password (e.g., Pass********). Users can access the full password only after beginning to track a domain under the Organizations tab.
To effectively utilize the tool, please follow these detailed steps:
-
Begin by clicking the Live Data Search tab.
-
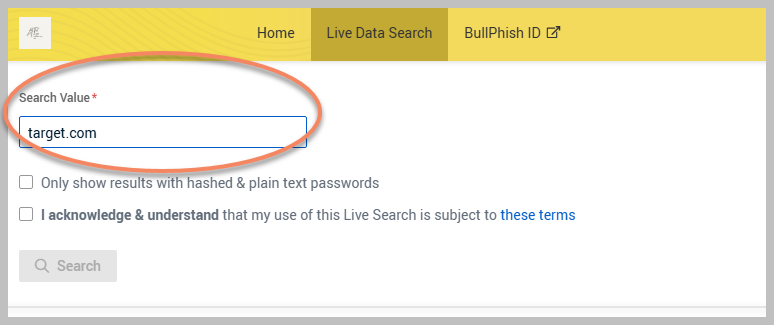
In the Search Value field, enter a domain name or an email address you wish to investigate. For example, you might input target.com or jdoe@bestbuy.com
-
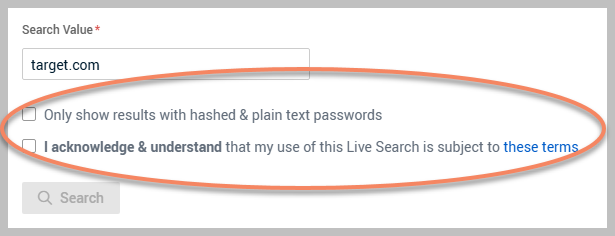
You will encounter two checkboxes on the search interface:
-
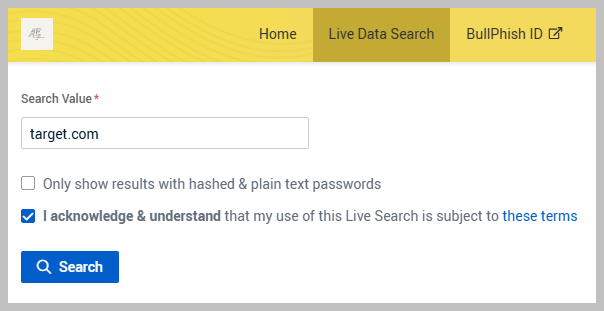
Ensure that you check the second checkbox to activate the Search button; this is a requirement for proceeding with the search.
-
After checking the necessary boxes, click the Search button to start the query.
-
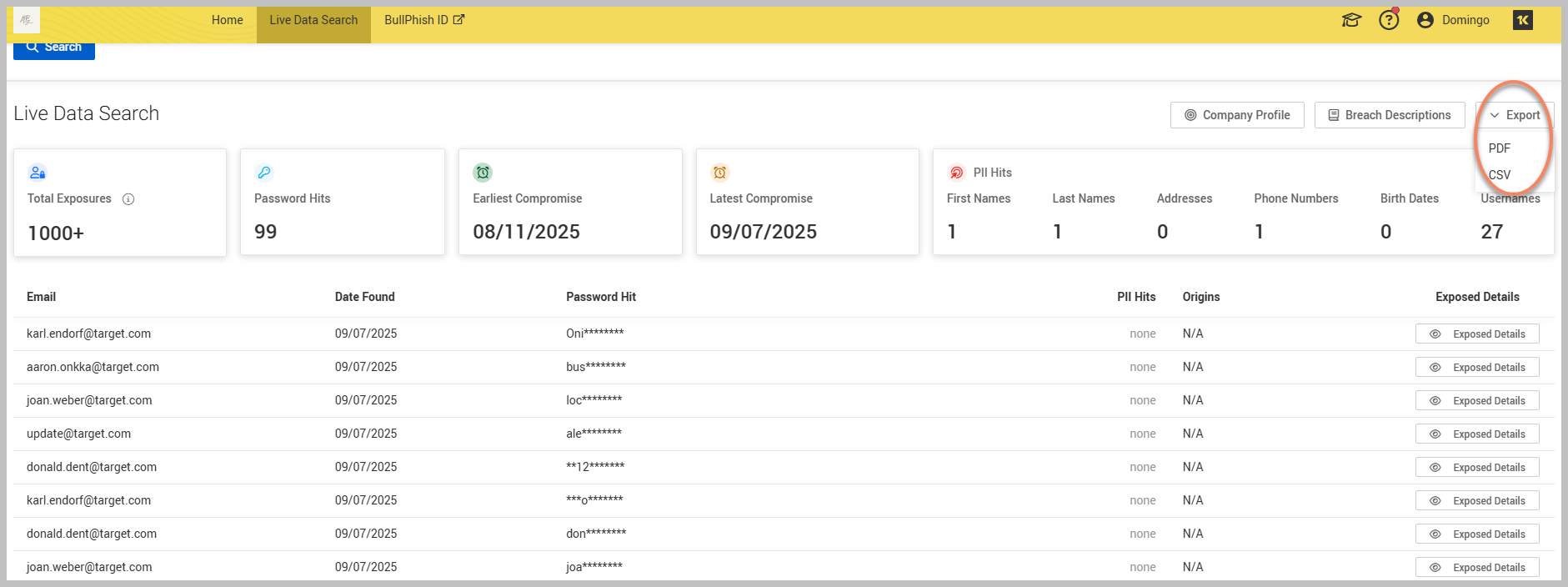
Once the search is completed, you will see results displaying the 100 most recent compromises related to the domain or email you entered. Additionally, the results will include the total number of compromises associated with that specific domain.
NOTE The message indicating that the search is displaying 100 of the 1000+ found results means that while over 1,000+ potential data breaches or security events were identified over the past two years, the platform is only showing you a limited, curated set of 100 results. Be aware that there might be a greater number of historical compromises accessible if you use the platform's domain monitoring feature.
-
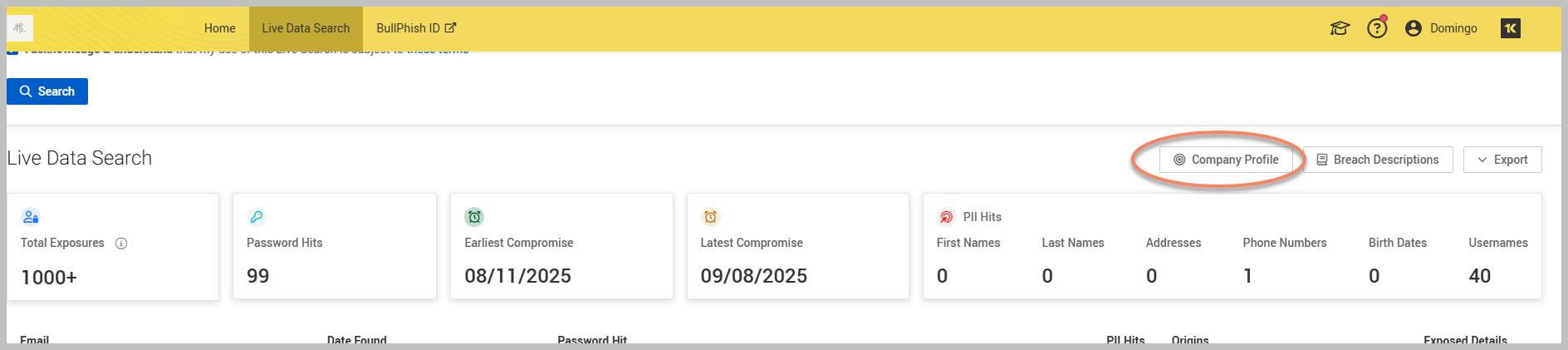
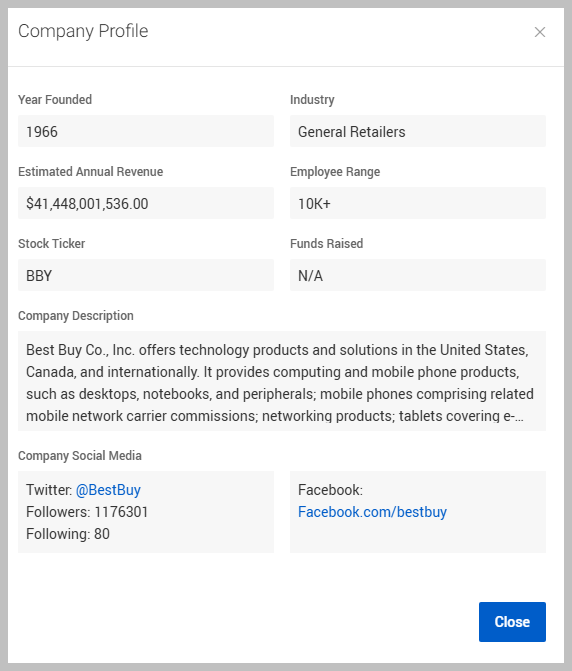
Click Company Profile to access detailed information about the company in question. The profile will typically include the following:
-
Year Founded
-
Industry
-
Estimated Annual Revenue
-
Employee Range
-
Description
-
-
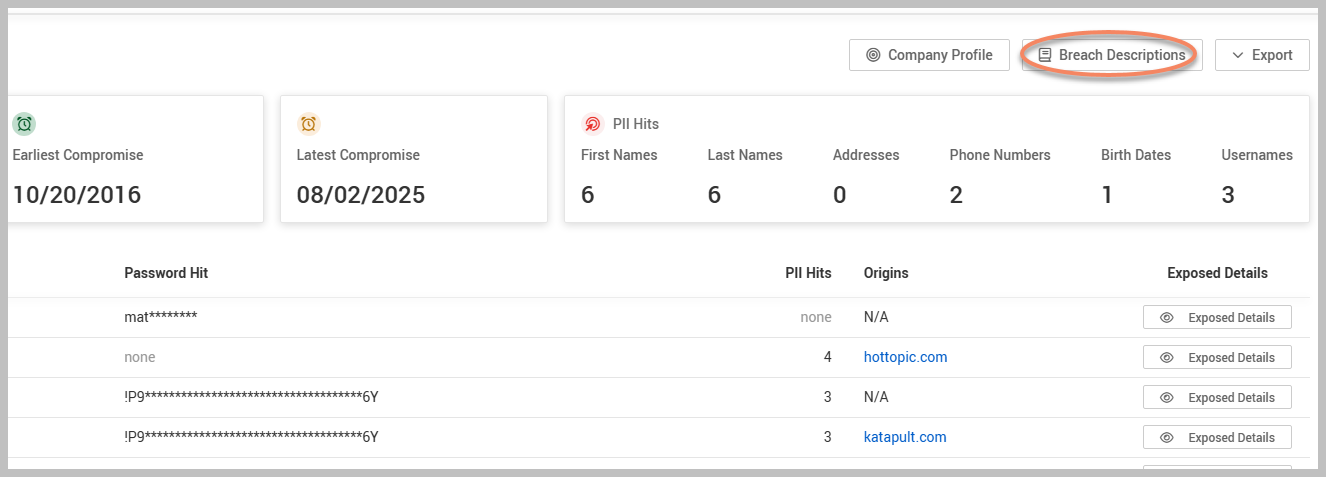
Clicking Breach Descriptions provides you with a comprehensive report detailing the data breaches that included the monitored information. The report encompasses information such as the following:
-
The name of the affected company.
-
The specific type of data that was compromised.
-
The date when the information was added to Dark Web ID.
-
The source of the data breach, helping you understand how the exposure occurred.
-
-
You can export all gathered data using the Export CSV and Export PDF options located in the upper-right corner of the interface. This feature is useful for saving the information for later review or for record-keeping. The exported results will provide as much attribution as possible, revealing additional personal information that may have been leaked onto the dark web, including related emails and passwords.
-
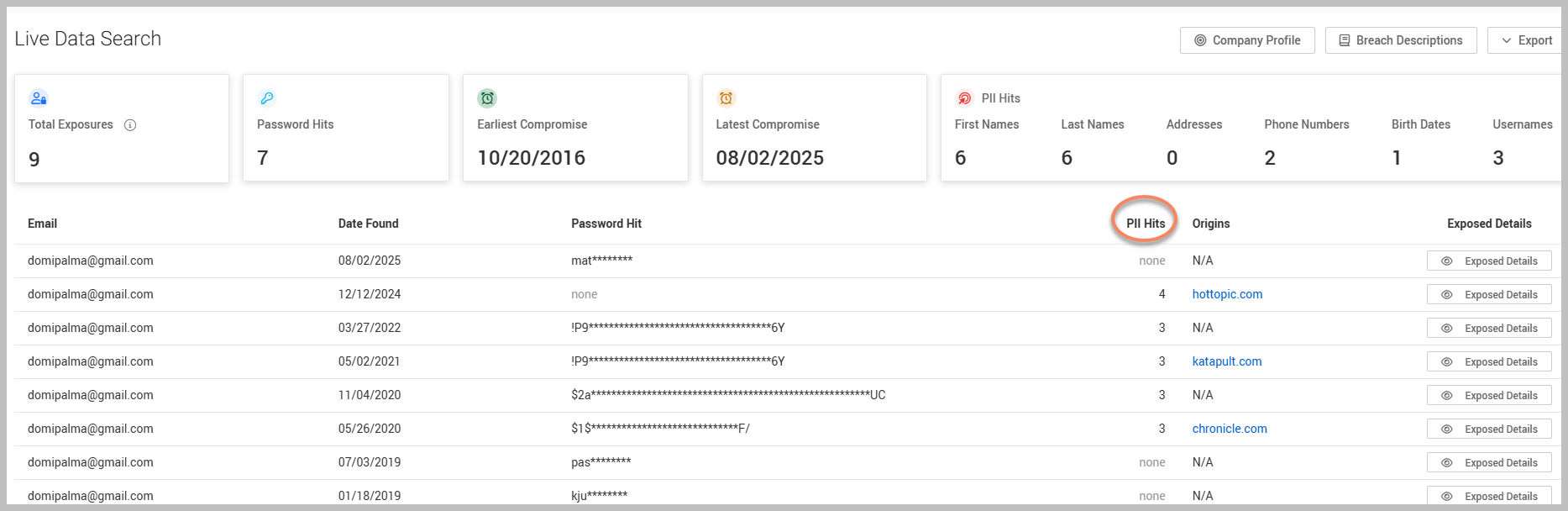
In the search results, there is a column titled Password Hit. Here, the first four characters of any discovered password will be displayed, followed by asterisks to obscure the rest. For instance, if the original password is Computer123, it will appear as Comp in the results. You can view the complete plain text of the password once you properly set up the domain within the Organization feature of the platform.
-
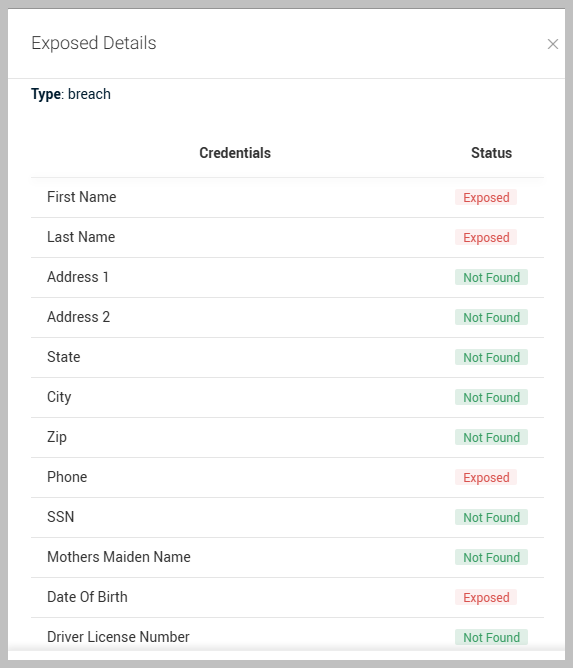
Another crucial column in the search results is labeled PII Hits, which stands for Personally Identifiable Information. When you see a PII Hit, it indicates that your personal information has been detected on the dark web due to a data breach. This exposure poses a serious risk, as cybercriminals may access sensitive information such as your name, address, phone number, and email address. Such details can facilitate identity theft, financial fraud, and unauthorized access to your online accounts. This information is considered PII because it can be used to uniquely identify you as an individual.
We have significantly broadened the categories of personally identifiable information (PII), increasing the total from 9 to 32. This expansion enhances the tool's capability to detect various compromises. The original PII categories supported included:
-
First Name
-
Last Name
-
Address 1
-
Address 2
-
City
-
Zip
-
Phone
-
Date Of Birth
-
User ID
The newly added PII categories are as follows:
-
State
-
SSN (Social Security Number)
-
Mother’s Maiden Name
-
Driver’s License Number
-
Card Type
-
Card Name
-
Card Number
-
Card CVN (Card Verification Number)
-
Card PIN
-
Card Expiration Date
-
Card Expiration Year
-
Card BIN (Bank Identification Number)
-
PayPal UID
-
eBay UID
-
Bank Name
-
Bank Route Number
-
Bank Account Number
-
Bank UID
-
Bank Password
-
Bank PIN
-
Medical ID
-
Medical Provider
-
Passport Number
-
By adding these new PII categories, users now have access to a more comprehensive set of data for monitoring and assessing potential compromises, thus enhancing visibility regarding the security of their financial and personal information.
-
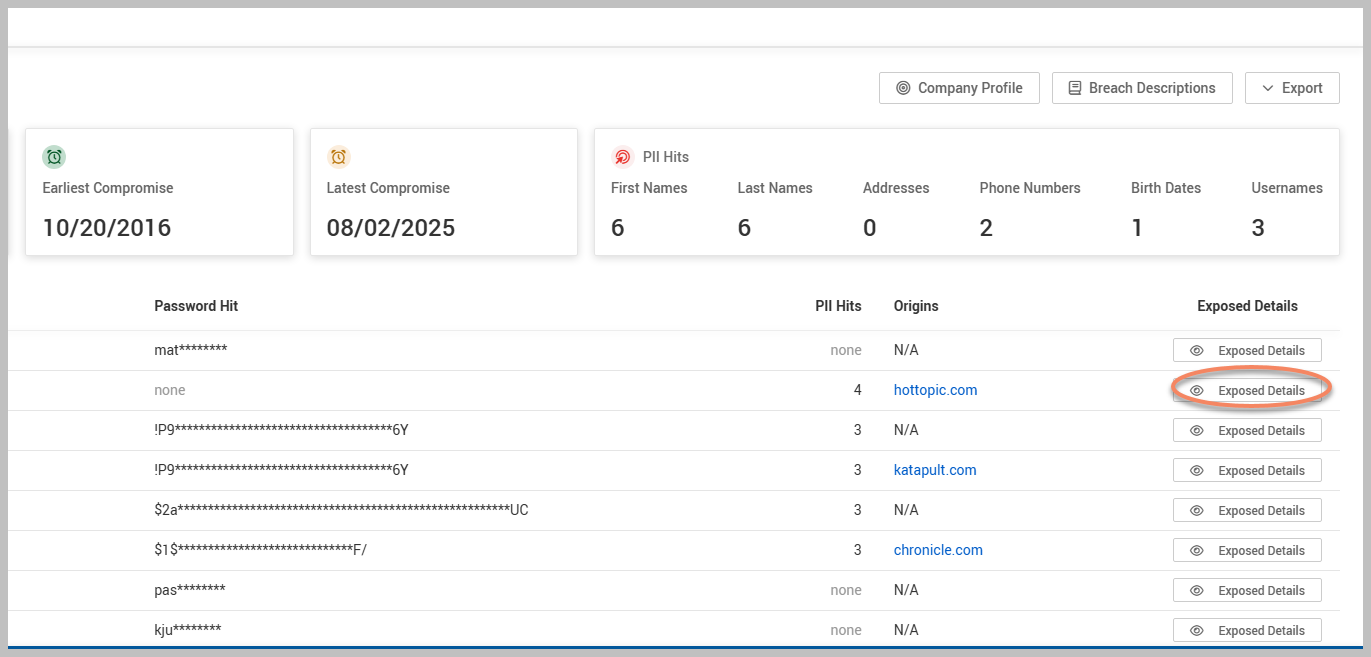
Lastly, for further insights into the specific details of any exposed data, you can click Exposed Details in the right corner of the interface.
This will provide additional context and information to help you understand the implications of any data exposures better.
By following these detailed steps, you can effectively navigate the tool and gain important insights into potential risks associated with data breaches involving your information.