Kaseya Spring Release: Dark Web ID
This page details each Dark Web ID release launched during the Kaseya Spring release.
Improvements
We are pleased to announce an improvement to our welcome emails for Small and Medium Business (SMB) users. To provide a more tailored experience, we will remove references to BullPhish ID for users who do not have access to this feature. This change will ensure that your welcome email is relevant and focused on the services available to you.
Fixes
We recently identified an issue where clicking Export All Compromises to CSV resulted in a file that could not be opened properly. This problem occurred when the organization's name contained certain special symbols. We are pleased to inform you that this issue has been resolved, and the exporting process now works as intended.
Fixes
We have successfully resolved the issue with organizational logos not displaying correctly in welcome emails, quarterly and monthly compromise notifications, and verification emails. The logos will now be prominently displayed in all relevant communications.
Enhancements
This release includes enhancements focused on security measures.
Fixes
We have addressed an issue regarding the Compromise Type column on the Organizational Compromises page and within the PDF and CSV compromise details reports. Previously, this column was left unpopulated when no value was available. Following this correction, it will now display the designation Not Disclosed instead of remaining blank.
Enhancements
The following are the key enhancements incorporated in this release:
-
We have implemented a couple of security updates.
-
We've strengthened the security of our API. With API v2, adding public domains to monitoring is no longer allowed to enhance protection and privacy. This update helps keep data more secure.
-
New welcome email templates have been created to enhance communication with new users, whether they are standalone users or already have a Kaseya One account. Our new welcome emails feature a more sophisticated design and provide more detailed information compared to our previous templates. Importantly, they include a reminder that Dark Web ID and BullPhish ID use the same login credentials. With these enhancements, we are committed to delivering a positive first impression and facilitating a seamless onboarding experience.
The following are the key enhancements incorporated in this release:
-
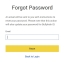
The Forgot Password page has been enhanced to provide clear and concise information regarding password updates. It now specifies that when a user updates their Dark Web ID password, this change will automatically update their BullPhish ID password as well. This integrated approach simplifies the password management process, ensuring that both accounts remain in sync and providing a streamlined experience for users.
-
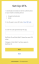
We have revised our password reset email template to enhance clarity, professionalism, and user-friendliness. The updated email enables users to reset their account passwords with confidence and assurance, as it includes a secure link that is valid for 48 hours and notes that Dark Web ID and BullPhish ID share the same credentials. It reiterates that resetting the password for one account will automatically reset it for the other.
-
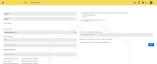
The 2FA setup windows have been enhanced with updated information clarifying that BullPhish ID and Dark Web ID operate under a unified 2FA configuration. As a result, the selected authenticator will be linked to both accounts, and they will share the same set of recovery codes. Any changes made to the 2FA settings in Dark Web ID will also be applied to BullPhish ID, ensuring consistent security measures across both platforms. Additionally, the reference to Passly as an acceptable authenticator has been removed from the system, streamlining the authentication process.
The updated information regarding the 2FA setup for Dark Web ID and BullPhish ID is also available on the My Settings page. The updated information confirms that Dark Web ID and BullPhish ID share the same two-factor authentication (2FA) setup: the chosen authenticator will secure both accounts seamlessly, you will have a single set of recovery codes for added convenience, and any changes made to the 2FA settings will affect both services. Moreover, Passly is no longer listed as an authenticator option.
Security enhancements
A user session will automatically conclude after 30 minutes of inactivity, resulting in the user being logged out. In the past, we implemented a longer session duration that did not account for specific periods of inactivity.
Fixes
Below are the key fixes implemented in this release:
-
In response to performance-related challenges, we have implemented a new fix that restricts the number of organizations to a maximum of 200 per daily/monthly notification.
-
In instances where users attempted to generate reports for organizations with a significant number of compromises, they encountered a 504 error.
To address this concern, a limitation has been established on the number of compromises that may be included in these reports. Upon clicking the Print Report button within an SMB organization, users will now see an Important note indicating that only the 1,000 most recent results will be presented in the compromise reports.
This note will also be featured on the first page of the reports.
The limitation is applicable in instances where there are more than 1,000 compromises within the specified reporting period and if the user has selected the Full Compromise Details checkbox.
dwid_thumb_0_64.png)